.NET Remoting introduction
.NET Remoting是在.NET中用於遠程方法調用的內置架構
.NET Remoting集成於.NET Framework中,允許所謂的遠程調用方法。客戶端和服務器之間支持的傳輸包括HTTP、IPC(命名管道)和TCP
以下是一個簡單的例子以進行說明:服務器創建並註冊傳輸服務器通道,然後將該類別註冊為服務
var channel = new TcpServerChannel(12345); |
客戶端只需要知道服務的URL,就可以透過遠程調用在客戶端和伺服器之間進行通訊
var remote = (MyRemotingClass)RemotingServices.Connect( |
.NET Remoting已於2009年隨著.NET Framework 3.0的發布而被棄用,並在.NET Core和.NET 5+中不再提供
Bypass DisableActivitySurrogateSelectorTypeCheck
衆所周知,ActivitySurrogateSelector gadget可以加載DLL,利用了System.Workflow.ComponentModel中的ActivitySurrogateSelector類別
但在DotNet framework(4.8+)fixed.
private sealed class ObjectSurrogate : ISerializationSurrogate |
我們可以看到,對GetObjectData函數進行了類型檢查,確保只能處理ActivityBind或DependencyObject
同時引入了一個新選項(DisableActivitySurrogateSelectorTypeCheck)
internal static bool DisableActivitySurrogateSelectorTypeCheck |
新增了一個新的方法呼叫NativeMethods.IsDynamicCodePolicyEnabled,確保只有當WLDP(Windows Lockdown Policy)被啟用時,類型白名單才會強制實施。這裏不需要關注WLDP(Windows Lockdown Policy)。這個AppSettings.disableActivitySurrogateSelectorTypeCheck選項實際上對應到 ConfigurationManager.AppSettings,通常指的是應用程式或web.config檔案中的策略
NamedValueCollection collection = ConfigurationManager.AppSettings; |
也就是說其實只需要反序列化payload觸發如下調用關閉保護
ConfigurationManager.AppSettings.Set("microsoft:WorkflowComponentModel:DisableActivitySurrogateSelectorTypeCheck","true"); |
TextFormattingRunProperties就可以輕鬆做到
using System; |
Remoting Internals
在客戶端連接到由伺服器提供的遠端物件時,它會建立一個實作指定類別MyRemotingClass的RemotingProxy。所有遠端的方法呼叫(除了GetType()和GetHashCode())都會以遠端呼叫的方式傳送到伺服器。當遠端的方法被呼叫時,代理會建立一個MethodCall物件,該物件包含方法和傳遞的參數的資訊,然後將其傳遞給chain of client sinks,以準備MethodCall並處理在給定傳輸上的遠端通訊
客戶端的默認chain of server sinks如下
HttpClientChannel:SoapClientFormatterSink → HttpClientTransportSink
IpcClientChannel:BinaryClientFormatterSink → IpcClientTransportSink
TcpClientChannel:BinaryClientFormatterSink → TcpClientTransportSink
在伺服器端,接收到的請求也會傳遞給chain of server sinks,其中也包括MethodCall物件的反序列化。它以dispatcher sink結束,該調度器接收器使用傳遞的參數來呼叫方法的實際實作。方法呼叫的結果隨後放入MethodResponse物件中,並返回給客戶端,客戶端chain of client sinks會反序列化MethodResponse物件,提取返回的物件並將其傳回RemotingProxy
伺服器的默認chain of server sinks如下
HttpServerChannel:HttpServerTransportSink → SdlChannelSink → SoapServerFormatterSink → BinaryServerFormatterSink → DispatchChannelSink
IpcServerChannel:IpcServerTransportSink → BinaryServerFormatterSink → SoapServerFormatterSink → DispatchChannelSink
TcpServerChannel:TcpServerTransportSink → BinaryServerFormatterSink → SoapServerFormatterSink → DispatchChannelSink
默認伺服器chain可以處理兩種格式。只有在通道未使用明確的IClientChannelSinkProvider或IServerChannelSinkProvider創建時,才會使用默認chain
MarshalByRefObject
如果類型擴展了MarshalByRefObject則表明為reference,該物件需要使用RemotingServices.Marshal進行marshal(編組)。該過程會將其注冊到當前的registry中,并且RemotingServices.Marshal將會返回ObjRef實例,這個實例持有關於編組物件的URL和類型信息
marshal的過程是透過RemotingSurrogate進行的,用於BinaryFormatter/SoapFormatter中(RemotingSurrogate.GetSurrogate(Type, StreamingContext, out ISurrogateSelector),CoreChannel.CreateSoapFormatter(bool, bool))
serialization surrogate允許自訂指定型別的序列化/反序列化
對於擴展自MarshalByRefObject的物件,RemotingSurrogateSelector會返回RemotingSurrogate(RemotingSurrogate.GetSurrogate(Type, StreamingContext, out ISurrogateSelector))
public virtual ISerializationSurrogate GetSurrogate(Type type, StreamingContext context, out ISurrogateSelector ssout) |
接下來按照.NET序列化機制,將會呼叫RemotingSurrogate.GetObjectData(Object, SerializationInfo, StreamingContext),最終會進入到
RemotingServices.MarshalInternal(MarshalByRefObject, string, Type)
internal static ObjRef MarshalInternal(MarshalByRefObject Obj, String ObjURI, Type RequestedType, bool updateChannelData, bool isInitializing) |
可以看到最後return objectRef,意味著每個擴展自MarshalByRefObject的遠程物件都會返回為一個ObjRef
在接收方,如果發送方傳遞的是一個ObjRef,在反序列化過程中最終將呼叫ObjRef實現的IObjectReference.GetRealObject(StreamingContext)
// This is called when doing fix-ups during deserialization |
該接口方法用於在反序列化期間使用由該方法返回值替換物件。對於ObjRef,此方法導致調用RemotingServices.Unmarshal(ObjRef, bool),它會使用反序列化后的ObjRef中指定的型別和目標URL創建一個RemotingProxy,當客戶端在這個代理上呼叫時,方法資訊和參數被打包成一個實作IMethodCallMessage的物件。這個物件被傳送到遠端進行處理,呼叫真實方法並將返回值(或異常)封裝在一個實作IMethodReturnMessage的物件中返回
也就是說所有擴展自MarshalByRefObject的物件都使用ObjRef按引用傳遞。並且在使用BinaryFormatter/SoapFormatter反序列化ObjRef后(不僅限於 .NET Remoting)會導致創建RemotingProxy(類似於yso中的jrmpclient)
Bypass TypeFilterLevel.Low
然而remoting services的remoting services默認為TypeFilterLevel.Low,那麽又該如何bypass
再重新説明下TypeFilterLevel.Low的限制
- Object types derived from MarshalByRefObject, DelegateSerializationHolder, ObjRef, IEnvoyInfo and ISponsor can not be deserialized.
- All objects which are deserialized must not Demand any CAS permission other than SerializationFormatter permission.
限制有兩種,一種是CAS,另一種是類別限制
CAS permission
PermissionSet currentPermissionSet = null; |
當前為SecurityPermissionFlag.SerializationFormatter,并且使用了currentPermissionSet.PermitOnly();意味著只能反序列化,其他諸如建立檔案都是不允许的
因爲在finally存在CodeAccessPermission.RevertPermitOnly();,可以理解爲解除了CAS Permitonly
也就是說只要在CoreChannel.DeserializeBinaryRequestMessage這一反序列化過程中不違反CAS就行,注意在這裏如果這時接收方獲取到ObjRef并且反序列化為RemotingProxy的時刻并不會直接觸發遠端連接,只有等到在對RemotingProxy的實際調用發生后才會建立遠端連接,所以說如果在此反序列化ObjRef是可行的
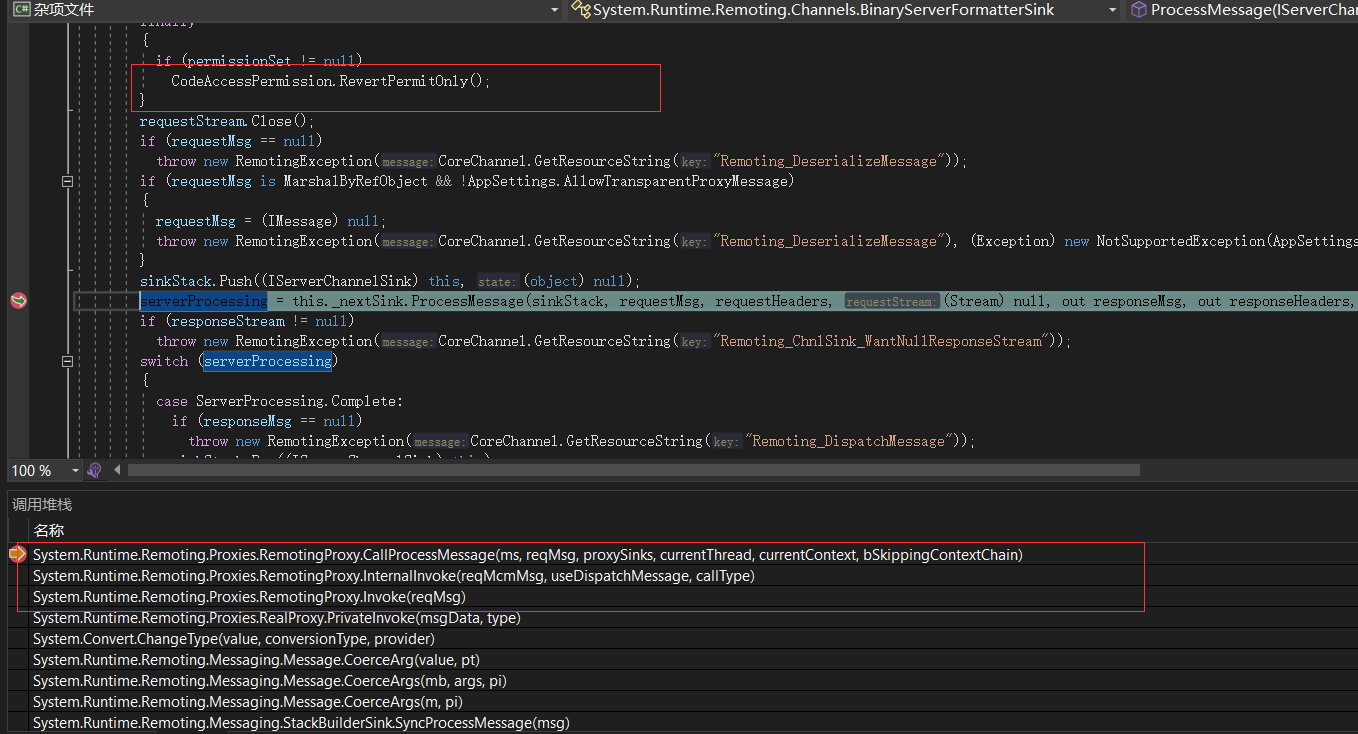
Call Stack中可以得知發生遠端調用(下面的紅色方框)這時已經是在CodeAccessPermission.RevertPermitOnly();后了
所以只需要在攻擊者端建立一個惡意類別并且擴展MarshalByRefObject並注冊,覆寫其中的方法使其被遠端調用后能夠返回自訂反序列化payload,這樣處理攻擊者返回的payload反序列化過程的將會移交給BinaryClientFormatterSink.DeserializeMessage(IMethodCallMessage mcm, ITransportHeaders headers, Stream stream)處理,這個方法沒有保護
還有一個細節是對RemotingProxy的實際調用是如何發生的,如果傳遞給方法的引數不是所需類型的直接對應,StackBuilderSink::SyncProcessMessage將呼叫 Message::CoerceArgs,嘗試將引數強制轉換為正確的類型。在這個Message::CoerceArgs中對於fall-back情況的處理是調用Convert::ChangeType,傳遞所需的類型和從客戶端傳遞的物件。接下來檢查傳遞的物件是否實作了IConvertible,並呼叫其中的ToType方法
所以説攻擊者只需要這樣
class SerializerRemoteClass : MarshalByRefObject, IConvertible{ |
類別限制
最後的一個問題是如何繞過類別限制
internal void CheckSecurity(ParseRecord pr) { |
private bool IsRemoting { |
internal void SetMethodCall(BinaryMethodCall binaryMethodCall) |
__BinaryParser.ReadMethodObject
internal void ReadMethodObject(BinaryHeaderEnum binaryHeaderEnum) |
解決方式為手寫協議,不要將MethodCall或者MethodReturn作爲top level record即可,這一部分可以參考
https://github.com/tyranid/ExploitRemotingService
接著是一個存在于real world中的簡單示例,僅僅使用到了前文提到的Bypass DisableActivitySurrogateSelectorTypeCheck
Addinprocess.exe
Addinprocess.exe存在於X:\Windows\Microsoft.NET\Framework\v4.0.30319(with Microsoft .NET installed)
Add-ins 實際上是.NET Framework提供的一種插件模型,使開發人員能夠為其應用程序創建插件。此模型通過在主機和add-in之間構建通信管道來實現此目的
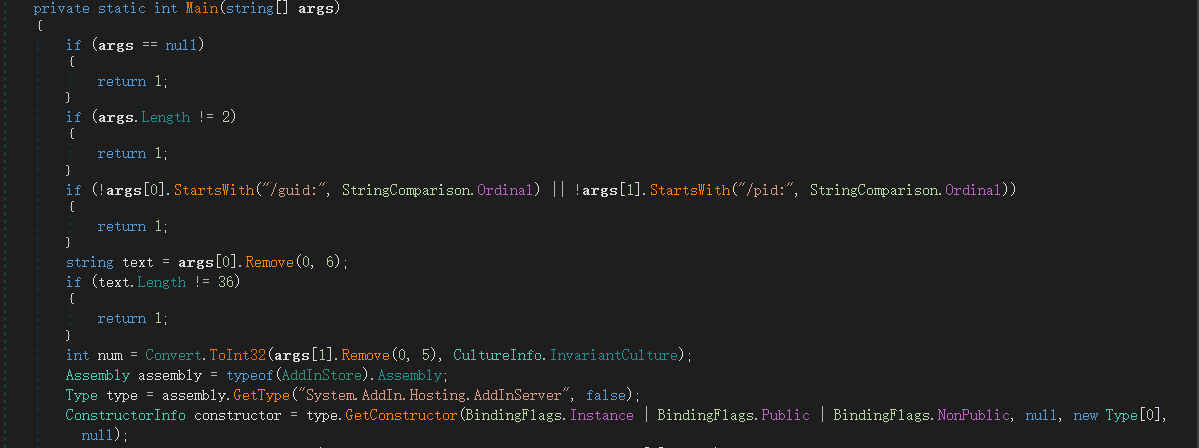
正如我們所看到的,需要提供/guid:[GUID]參數和/pid:[現有 PID]參數
/guid參數由你提供,並被用作IPC通道名稱。**/pid**參數則是指一個已經運行的進程的進程識別號,addinprocess.exe 會等待其退出
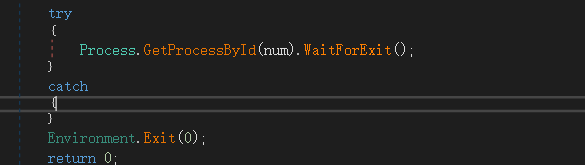
接著,註冊.NET Remoting通道,可以看到addinprocess.exe 使用的是TypeFilterLevel.Full
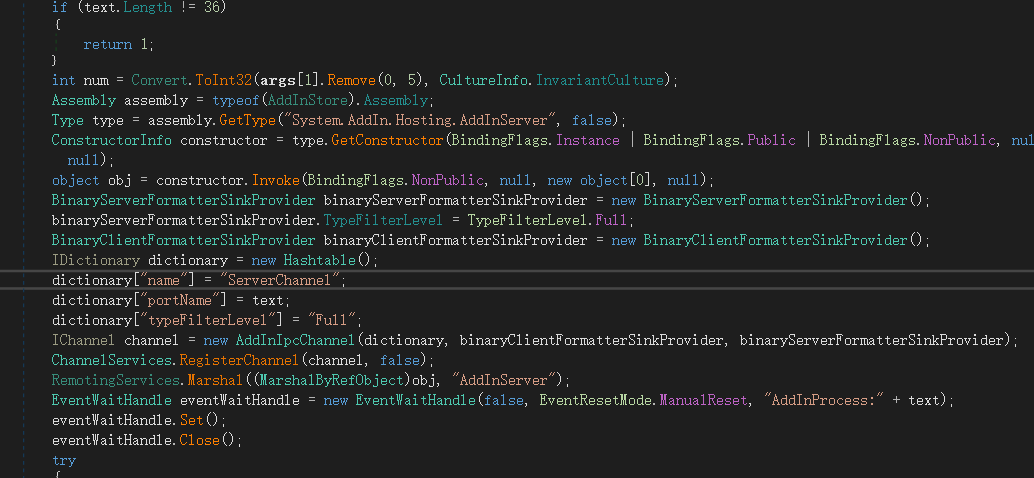
攻擊手法如下
- Addinprocess.exe /guid:xxxxxxxx /pid:xxxx(imma pid of explorer.exe)
- type DisableActivitySurrogateSelectorTypeCheck.bin > \.\pipe\xxxxxxxx
- type ActivitySurrogateSelector.bin > \.\pipe\xxxxxxxx
廢話收容所
當作自己學習下面文章記錄的一篇學習筆記,方便回憶
https://codewhitesec.blogspot.com/2022/01/dotnet-remoting-revisited.html

